ZERO Trust is a straightforward concept – trust nothing, verify everything. Successful implementation can be difficult though, because retrofitting legacy systems may not be an option, and all-in-one ZERO Trust products do not exist. Configuring your network and systems for ZERO Trust to the best of your ability is the beginning, not the end of the journey.
Integrity Monitoring
Systems, user roles, and technical resources change. Continuous verification and real-time monitoring are necessary to confirm controls remain effective when changes occur.
XYPRO Technology and HPE provide security solutions for end-to-end security of NonStop systems. This includes tools for three of the highest-value monitoring you can implement.
- Continuous Integrity Monitoring for awareness of changes, expected or otherwise, on your NonStop systems.
- Real-Time Monitoring and Alerting for high-risk or suspicious activities, for example, the logon of newly created users with elevated permissions.
- Monitoring of NonStop appliances, such as CLIMs and NonStop consoles.
XYGATE SecurityOne (XS1) Integrity Monitoring provides change detection for frequently used object types for HPE NonStop systems. XS1 Security Intelligence Suite delivers real-time, continuous monitoring for a diverse set of high-risk activities (for example, suspicious logins, changes to ProgID or License status, or use of a frozen account to name a few). XS1 Appliance Sentry Monitor scans and reports on CLIMs and NonStop consoles.
Below are examples of XS1 Integrity Monitoring and how it supports your ZERO Trust strategy.
For those of you using XYGATE Compliance Pro (XSW) it has been a reliable monitoring tool for many years, and it does a very good job, but XS1 is a big step up from XSW and offers enhanced real-time monitoring along with new, cutting-edge functionality.
XYGATE SecurityOne (XS1) Integrity Monitoring:
Integrity monitoring in XS1 is a simple, three-step process:
- Choose the type of monitor you want to create,
- Define the objects you want to be monitored and
- View the results.
File masks and filters can be used to narrow the focus of your monitoring to the individual Guardian Files if desired.
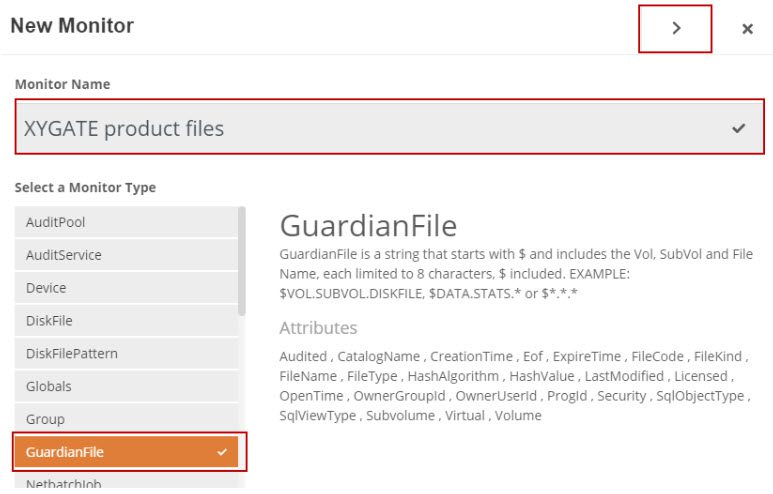
Step 1: Add Monitor, define the type of monitor (Guardian File for example) and provide a name for the monitor:
Step 2: Define the systems to monitor, define the file masks for files to include or exclude, set the frequency of the monitoring, and save the monitor.
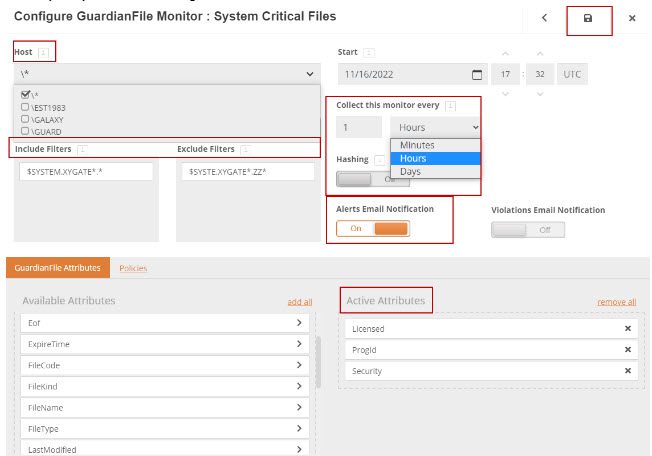
The monitor shown here will collect all Guardian File attributes but will only create an alert when the file security has changed or if the Licensed or ProgID on the file changed.
In the future, when more XYGATE products are added to $SYSTEM they are automatically part of the collection criteria and will be added to the generated report.
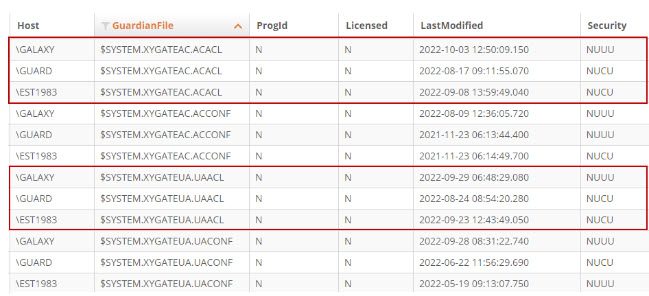
Step 3: View the monitoring reports. The results displayed are for all monitored NonStops and include every file in each $SYSTEM.XYGATE volume, excluding any temp files (files starting with ZZ).
The reported results can be sorted, filtered, and customized to display only attributes of interest. The report below makes it easy to identify how the security differs for the ACACL, ACCONF, UAACL and UACONF files across the three NonStop servers. R-Click to export the results to share the findings with your operations or security teams.
XYGATE Compliance Pro – Integrity Monitoring:
By contrast, XYGATE Compliance Pro requires several steps before your first report can be viewed.
1. Define your collection criteria (NonStop systems and what disks to monitor).
2. Create a new integrity check for each of the four files (ACACL, ACCONF, UAACL and UACONF).
a. Create a new integrity check using the System Integrity Rule Builder.
b. Build a rule to monitor the XYGATE files of interest. Using the System Integrity Rule Builder you can select “Guardian Files” as the Entity to check.
c. Filter for the Volume of interest, find the subvolume containing the files of interest
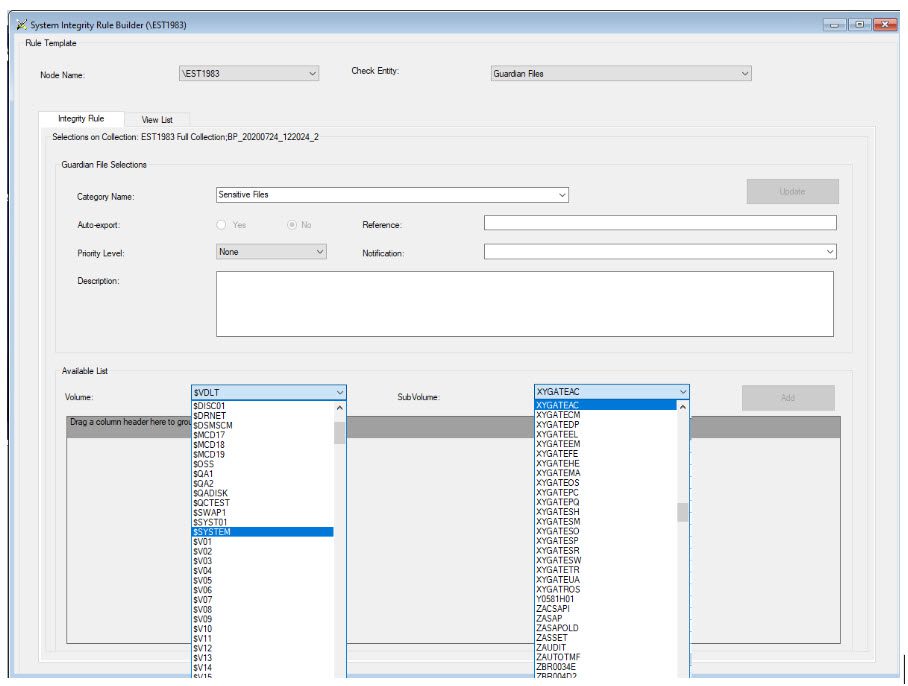
d. Scroll through the list of files to find the files you want to select and monitor.
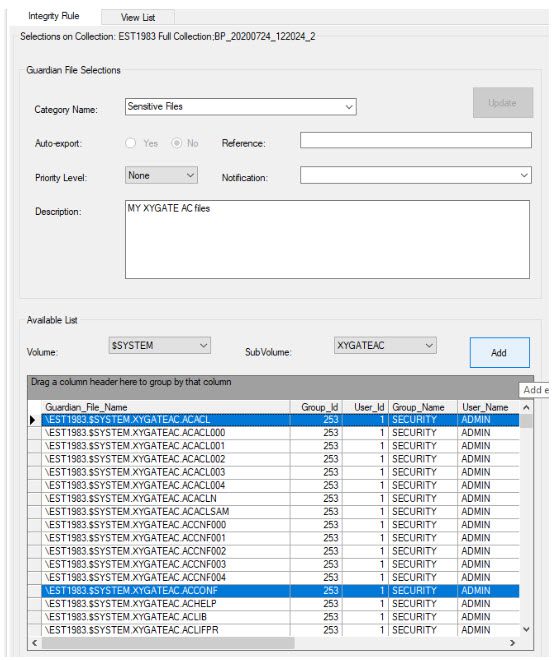
e. Add selected files to the integrity monitor.
3. Repeat steps a-e for XYGATEUA.
4. Run the collection.
5. Load the collection.
6. View the results.
The results are presented in a table displaying every Guardian File attribute. Columns cannot be removed from the table to optimize the information displayed as was done with XYGATE SecurityOne.
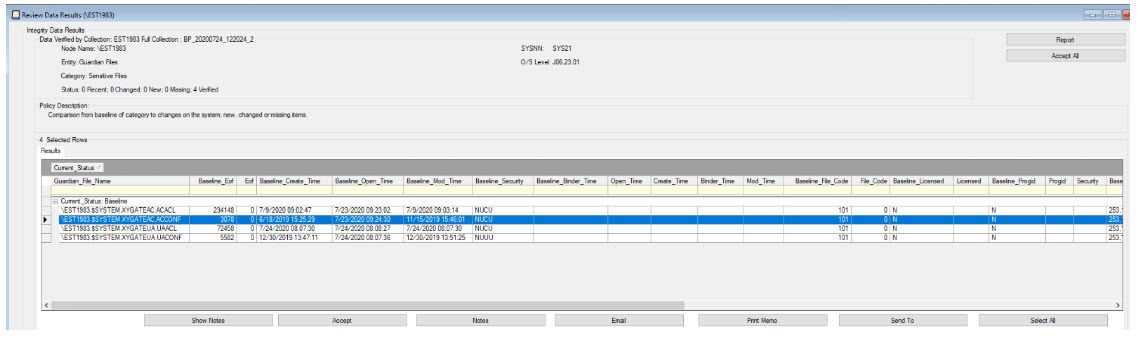
You can see how XYGATE SecurityOne automates, simplifies, and provides intelligent integrity monitor results.
XS1 Increases Staff Productivity
Most organizations cannot allocate enough resources to proactively monitor their environment. Instead, security staff must devote time at the back end, investigating possible incidents – a very manual and time-consuming process of collecting, correlating, and searching through disparate logs. XS1 automates incident identification by correlating and contextualizing data in real-time and highlighting actionable incidents that need immediate attention. This patented XS1 functionality means you’re not wasting time on “Possible” events. This automation of investigative activities frees up nearly 80% of your staff’s time, allowing them to focus on proactive monitoring.
XS1 Modernizes Security Resources
The sheer processing power of HPE NonStop systems grows to support increasing volumes of work and critical assets being protected. HPE NonStop systems and the functions they perform are integral to the global financial infrastructure. Properly Securing these mission-critical workloads, and having only a few staff members familiar with NonStop security management increases the risk of insider abuse. The differentiator for such a modern product like XS1 is that security management experience means you’ll find it intuitive to use XS1 to manage HPE NonStop security without needing in-depth NonStop knowledge, greatly reducing the risks from resource attrition and insider abuse.
Learn more about the benefits of XYGATE SecurityOne
Visit our XYGATE XS1 product page for more information.
For more information and to schedule a demo about Real Time integrity monitoring, contact us at https://xypro.com/contact/

